
Student accounts may be hit by more than tuition charges this semester.
University email accounts are increasingly the targets of scammers impersonating other people to trick recipients into revealing information that can be used for profit. Eighteen reported email phishing attacks have been reported at Chapman since Jan. 17, according to the Information Services & Technology (IS&T) website. Phishers spoof senders with the objective of shaking down their targets, getting access to other accounts to suck out money or to obtain confidential info and wage malware attacks. Phishing scams are becoming more sophisticated and harder to detect. Chapman is trying to address the problem by sending staff fake emails to see if recipients are savvy enough to identify them. If staff fails, they’re told to take a training class.
A Harvard professor realized it wasn’t really the dean emailing him with requests for $500 Amazon gift cards during an alleged Saturday afternoon meeting last year. The professor had some fun with his would-be tormenter, asking the self-described “dean” why her administrative assistant couldn’t help and engaging in lofty talk about the dean’s research. “Tell me what you consider to be the single most important finding is in your QJE article on the FAFSA as a barrier to college attendance. I love that paper and feature it prominently on my syllabus,” he wrote. Needless to say, he never sent the gift cards.
“Phishing numbers were up in nearly every industry in 2018,” according David Nield, a tech and cyberware author.
Phishing is a social engineering technique used by cyber criminals to “trick users into providing their personal information such as usernames, passwords, credit card details and social security numbers by pretending to be a trustworthy entity,” according to IS&T. “Phishing emails can be used to compromise an individual’s personal information or an institution’s infrastructure and proprietary information.”
When Alexis Blumenthal received a Chapman email threatening sextortion, she called her twin brother in a panic. The junior graphic design major had been targeted by a cyberattack that demanded $500 in Bitcoin if she didn’t want compromising pictures of herself broadcasted to everyone in her contact list.
“I freaked out and almost gave in,” Blumenthal said. “They emailed me twice and were threatening to send nude photos to my contacts.”
She didn’t know what photos they could have, but she didn’t want to take any chances. Still, she began investigating Bitcoin. Anything can be photoshopped and the hackers had access to her contacts, she said.

Blumenthal received a total of three threatening emails and debated paying the ransom. Ultimately, after conferring with her family, she decided to delete the emails and change the password to her Chapman email account. She didn’t receive any more emails and never reported her experience to university officials, she said. By the time she thought of doing so, she had permanently deleted the email threats.
Being more informed about cybersecurity precautions would have saved her a lot of trouble, Blumenthal said.
More than 100 schools and businesses were victims of cyberware attacks by the end of 2018, according to a study by The Business of Federal Technology. Hackers attempted to sell more than 100 million private records, some of which were obtained via threats of violence, according to a 2019 industry warning by the FBI and the Department of Education inspector general. The warning emphasized the importance of strong information technology (IT) systems at targeted institutions.
Cyber criminals use multiple tactics to obtain access to sensitive information, but the most common is phishing scams and malicious software (Malware) attacks, according to Cisco, a company that provides IT services.
Sixty-six percent of malware is installed through malicious email attachments and 70 percent of cyberattacks use a combination of phishing and hacking, according to a Verizon Breach Data Report.
Malware infections can include spyware, ransomware, viruses and worms that breach networks by clicking malicious links or email attachments. Once clicked, breaches in the system can block access to networks (ransomware), install harmful software, access and transmit sensitive information on hard drives (spyware) or damage the system, according to Cisco.
“Spear phishing” is a favorite of scammers who target Chapman. This form of cyberattack targets particular individuals, according to Nield, and customizes emails to resemble correspondence coming from a legitimate sender.
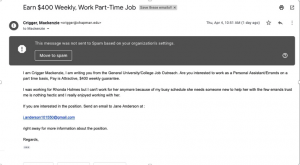
A seemingly-legitimate Chapman email was sent on April 4 that lured students to forfeit banking information by offering a paid-weekly position, according to an email sent by Dean of Students Jerry Price. The email urged interested students to reply to “Jane Anderson.” If they did, they received a request for banking information so a check could be deposited. They would then send a fraudulent check and request a lesser amount be sent to a third account, supposedly a client, which would charge students’ personal accounts. Students who responded to the first email only shouldn’t have been affected, Price said.
“Please be wary of any ‘too good to be true deals,’” Price wrote in his April 8 weekly announcement.
“If phishers can engineer access to an email inbox inside a company, they can produce emails that don’t just look as if they come from a genuine source, but that to all extents are from a genuine source,” Nield said.
Spear phishing attacks impersonating President Dr. Daniele Struppa on March 8 and the Dean of Wilkinson, Dr. Patrick Fuery, on Jan. 3 were sent to Chapman staff and faculty this year.
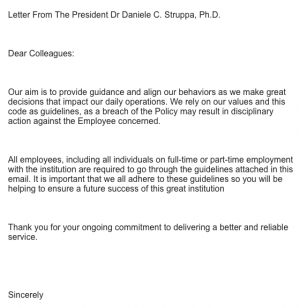
Spear phishing imitates people of authority, like Struppa, because people are more trusting and willing to follow through with proposed actions. Phishing email impersonating President Dr. Daniele Struppa on March 8, 2019. Photo from IS&T.
“When you get an email from somebody you know and trust you don’t question it,” Nield said.
Cyberware attacks often target college students and faculty around times when funds are being distributed to students accounts, according to an email from Price warning about the cyber attacks.
“Colleges have a lot more public information than most businesses,” Nield said. “That gives the attacker more resources they can use to fool people into things like this.”
Over 20 Chapman staff and faculty accounts were affected in a critical security breach on Oct. 3, 2018, Jamie Ceman wrote in an email. The email, which claimed to be from the university, contained a link that required the input of Chapman credentials, providing the attackers with access to institutional accounts that contained sensitive banking information. The hacker re-routed payroll checks for three employees, the email stated. The employees were reimbursed for the paychecks, said Ceman who declined to identify the three employees.
Links aren’t the only way scammers gain access to personal information.
In addition to being cautious about clicking links, junior computer science major Haley Anderson does three things to protect herself from malware attacks: she updates her software constantly, only connects to secure WiFi networks that require passwords and changes her passwords frequently.
“There are codes that virtually anybody can create, if they know what they’re doing, to gain access to somebody’s information if they fall for it,” Anderson said. “I’m extra careful because I’m more informed about that kind of thing.”
Cyber criminals don’t even need to trick users, they create breaches through public domains.
Areas of public domain – including free public WiFi – is what IS&T considered “high-risk data.” This is easily accessible information that, when connected to the domain, makes users vulnerable to hackers because websites aren’t secured or password protected. High risk data is considered public information, like published research. It is information on the internet that’s available without required authentication – such as job postings and other public domains, according to IS&T.

Eighty-two percent of millennials reuse passwords, and 42 percent will only change their password when forced to, according to a 2017 study by First Data. Seventy-two percent of millennials have connected to a public WiFi network that is not password protected, according to a 2014 study by Raytheon.
Free public WiFi that doesn’t require authentication, like a password, is desirable for consumers and hackers because it requires no authentication to establish a network connection. This creates opportunities for hackers to gain access to all information being sent out on the connection, or distribute malware, according to Nield.
“I never think about the security of my phone or laptop when I connect to public WiFi,” said Jason Weigel, a junior business administration major. “I just think, ‘oh cool, free WiFi, I won’t blow up my phone data.’”
In caution of all risks, IS&T is taking steps to prevent cyberware attacks on Chapman accounts.
To help protect sensitive data, IS&T has employed a new system, ProofPoint, that protects links sent to Chapman emails. It works by first sending the link to ProofPoint to detect whether or not the site is malicious, then directs the user to the URL if it’s not, according to IS&T.
To prevent cyberattacks on user accounts, IS&T also implemented Multi Factor Authentication using the Microsoft Authenticator app, according to Chapman’s website.
“[Two-factor authentication] is no guarantee of protection against phishing, but it does raise the bar for hackers trying to get at your stuff,” LaCour said.
The website also outlines characteristics to help users spot fraudulent emails that: urge you to click a link, enter a username and password, requests to transfer money, get gift cards, send personal information and have poor wording or phrasing.
IS&T urges students to forward any suspicious or malicious messages to them as an attachment at abuse@chapman.edu.
